It’s beginning to look a lot like… well you know the rest. ‘Tis the season for a cloud forecast.
Google, Palo Alto Networks’ Cloud IDS Goes Live
Google Cloud this week made Cloud IDS generally available with several additional features compared to when it first announced the network-based threat detection with Palo Alto Networks in July.
The managed service, built on Google Cloud infrastructure, uses Palo Alto Networks’ threat-detection technologies to helps organizations detect network-based threats and meet compliance standards that require an intrusion detection system.
Specifically, it uses Palo Alto Networks’ VM-Series firewalls, backed by its Unit 42 security research team. The vendor’s threat-analysis engine continually updates the catalog of known threats and uses anomaly detection for unknown threats. 
Palo Alto Networks’ threat-analysis engine processes about 15 trillion transactions per day, Muninder Singh Sambi, SVP of product management, said in an earlier interview with SDxCentral.
“We also have the industry’s best threat intel team,” he added, referring to the vendor’s 200-plus-member Unit 42 organization. “You can think of them as the threat ninjas that look at all of these transactions that we see and are able to provide valuable insights as to whether these are threats or benign requests.”
Additionally, the general availability release includes:
- Service available in all regions
- Auto-scaling available in all regions
- Detection signatures are automatically updated daily
- Support for customers’ HIPAA compliance requirements (under the Google Cloud HIPAA
- Business Associate Agreement)
- ISO27001 certification (and in the audit process to support customers’ PCI-DSS compliance requirements by year-end)The new product also integrates with Google’s Chronicle security analytics platform, which the cloud giant says helps companies investigate threats surfaced by Cloud IDS.
Source: SDX CENTRAL
24 Biggest Mergers & Acquisitions, divestitures and refocus…and some that important updates that you probably missed in 2021!
Here are the top five on the list.
Sangoma kicked off 2021 with the announcement of its $437 million acquisition of Star2Star.
The transaction helped vault Sangoma back into the conversation as a leading cloud communications provider. It built on Sangoma’s previous acquisitions of Asterisk PBX software provider Digium and CPaaS provider VoIP Innovations. The deal, however, was just a taste of the musical chairs of UCaaS consolidation that would occur in 2021. 
HPE announced the acquisition of Zerto, designed to bolster its as-a-service strategy.
HPE will attach Zerto’s cloud data protection and management tools to HPE GreenLake cloud data services, according to HPE’s CEO.
It cost $374 million for HPE to buy Zerto.
Citrix bought workplace management platform provider Wrike.
The $2.25 billion deal crossed the news wires in January. Adding Wrike helps Citrix better automate and simplify the experience of employees using Citrix Workspace. Citrix’s CEO also said Wrike will help Citrix customers move to the cloud faster.
Symphony Technology Group (STG) is merging together two prominent cybersecurity organizations.
McAfee in July announced the completed $4 billion sale of its enterprise business to the consortium. At around the same time, FireEye (now known as Mandiant) sold its products business to STG for $1.2 billion. In the meantime, McAfee accepted a $14 billion acquisition that will take it private. 
MSP Corp Investments bought Canadian MSPs in 2021.
The group has been wielding more than $50 million in capitalization to attract MSP owners who want to sell their business. They can stay in the business or retire if they like. MSP Corp’s president said deals typically close within 90 days.
Check out the full list at Channel Futures.
Source: Channel Futures
Apache Log4j recently disclosed a new RCE issue
We are writing to notify you that Apache Log4j recently disclosed a new RCE issue CVE-2021-44228 that affects all versions from 2.0-beta9 to 2.14.1 [1]. This issue could be relevant to your products offered through AWS Marketplace. If your product uses Apache Log4j, AWS recommends you mitigate this issue by following the suggested fix below or by upgrading Log4j to version 2.15.0. Please submit a new version of your AMI/Container/SageMaker products that fixes this security issue and restrict the affected version as soon as possible.
Issue details:
As noted in the security advisory from Apache log4j, in Apache Log4j2 versions from 2.0-beta9 to 2.14.1 JNDI features used in the configuration, log messages, and parameters do not protect against an actor controlled LDAP and other JNDI related endpoints. An actor who can control log messages or log message parameters can execute arbitrary code loaded from LDAP servers when message lookup substitution is enabled. From Log4j 2.15.0, this behavior has been disabled by default. So, this issue would be relevant to any product that uses Apache Log4j2 2.0-beta9-2.14.1.
Suggested fix:
In Apache Log4j versions 2.10 – 2.14.1, this behavior can be mitigated by setting system property “log4j2.formatMsgNoLookups” to “true” or by removing the JndiLookup class from the classpath (example: zip -q -d log4j-core-*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class). Java 8u121 [2] protects against RCE by defaulting “com.sun.jndi.rmi.object.trustURLCodebase” and “com.sun.jndi.cosnaming.object.trustURLCodebase” to “false”. For versions prior to 2.10 this behavior can be mitigated by upgrading to version 2.15.0.
For any questions, please reach out to the AWS Marketplace Seller Operations team.
Refernces
[1] https://logging.apache.org/
[2] https://www.oracle.com/java/
[3] https://aws.amazon.com/
SOLUTION – Using AWS security services to protect against, detect, and respond to the Log4j vulnerability
This covers what you can do to limit the risk of the vulnerability, how you can try to identify if you are susceptible to the issue, and then what you can do to update your infrastructure with the appropriate patches.
The Log4j vulnerability (CVE-2021-44228, CVE-2021-45046) is a critical vulnerability (CVSS 3.1 base score of 10.0) in the ubiquitous logging platform Apache Log4j. This vulnerability allows an attacker to perform remote code execution on the vulnerable platform. Version 2 of Log4j, between versions 2.0-beta-9 and 2.15.0, is affected.
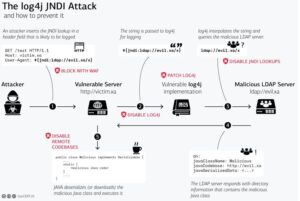
The vulnerability uses the Java Naming and Directory Interface (JNDI) which is used by a Java program to find data, typically through a directory, commonly an LDAP directory in the case of this vulnerability.
Customers can use multiple AWS services to help limit their risk/exposure from the Log4j vulnerability. Customers can build a layered control approach, and/or pick and choose the controls identified below to help limit their exposure.
Contact eCloud Managed Solutions to help walk you through this or any other AWS solution for your environment.
Figure 1, below, highlights the Log4j JNDI attack flow.
AWS vs Azure vs GCP Cloud Comparison: Databases
Before we dive in, there were a few fundamental concepts worth knowing when it comes to databases. The answers await you in this cloud provider comparison guide!
- Vertical scaling — Vertical scaling is where you have a single database instance that grows by adding more compute, memory, and/or storage so that it can handle more traffic.
- Horizontal scaling — Horizontal scaling is where you add multiple database instances so the traffic that hits your database gets distributed across those instances. This can scale much more than vertically, but it’s hard to do because it requires data to either be deterministically split between the instances or kept in sync between those instances — both of which create complexity around things like data, structure, consistency, and atomicity.
- Read replicas — Some database services will allow you to scale horizontally for read-only operations via read replicas. Here, data is synchronized for read-only purposes between multiple instances, but you’ll still have a single primary instance for write operations.
The next concept to understand is availability. Availability is where the cloud providers offer a service level agreement (SLA) for how long the database will be up and running to receive requests within a given time period.
- If a database has an availability SLA of 99.9%, it can have a downtime of 44 minutes in a month. Whereas if a database has a 99.999% SLA (aka known as five nines) it can have 26 seconds of downtime a month.
Cloud providers apply high-availability architectures to allow for fault tolerance across a subset of the various failure modes. Depending on your specific needs, you’ll want to balance availability, cost, and features to decide which service is best for you.
Get all the clarity on databases in this blog from Cloud Guru
WE ARE MIGRATION ACCELERATION PROGRAM (MAP) ELIGIBLE and CERTIFIED
So what does that mean for you? We can get you more money to offset the cost of migrating to AWS and have proven to AWS engineering that we can migrate our clients successfully to and from anywhere! Organizations migrating to AWS require expertise, tools, and alignment of business and IT strategy. Many businesses can accelerate their migration and time to results through partnering with eCloud while reducing migration costs.
Get Started
Speak with a cloud consultant today.
eCloud dramatically simplifies backup and recovery by consolidating multiple point products on a single software-defined platform that spans from on-premises, enterprise edge, and to the public cloud. Architected on web-scale principles, eCloud can natively run in the public cloud and offers comprehensive protection against ransomware. We future-proof our backup and recovery strategy whether you’re on-premise, hybrid, or fully in the public cloud.
Typically, eCloud helps customers reduce their TCO by 50 to 70% with our proven solutions.
Author: Eric Sanders, Managing Partner

________________________________________________________________________




